In an era where connectivity is the heartbeat of our daily lives, the advent of embedded SIM cards, or eSIMs, has revolutionized the way we stay connected. However, as with any technological advancement, questions loom over the security of eSIMs. Can they be hacked, or worse, tracked? Let’s unravel the intricacies of eSIM security to separate fact from fiction in the article below. But first, for those seeking reliable and secure eSIM plans in Europe, exploring options like those offered at https://telesim.com/esim-plans/europe can provide valuable insights and peace of mind.
Understanding eSIM Technology
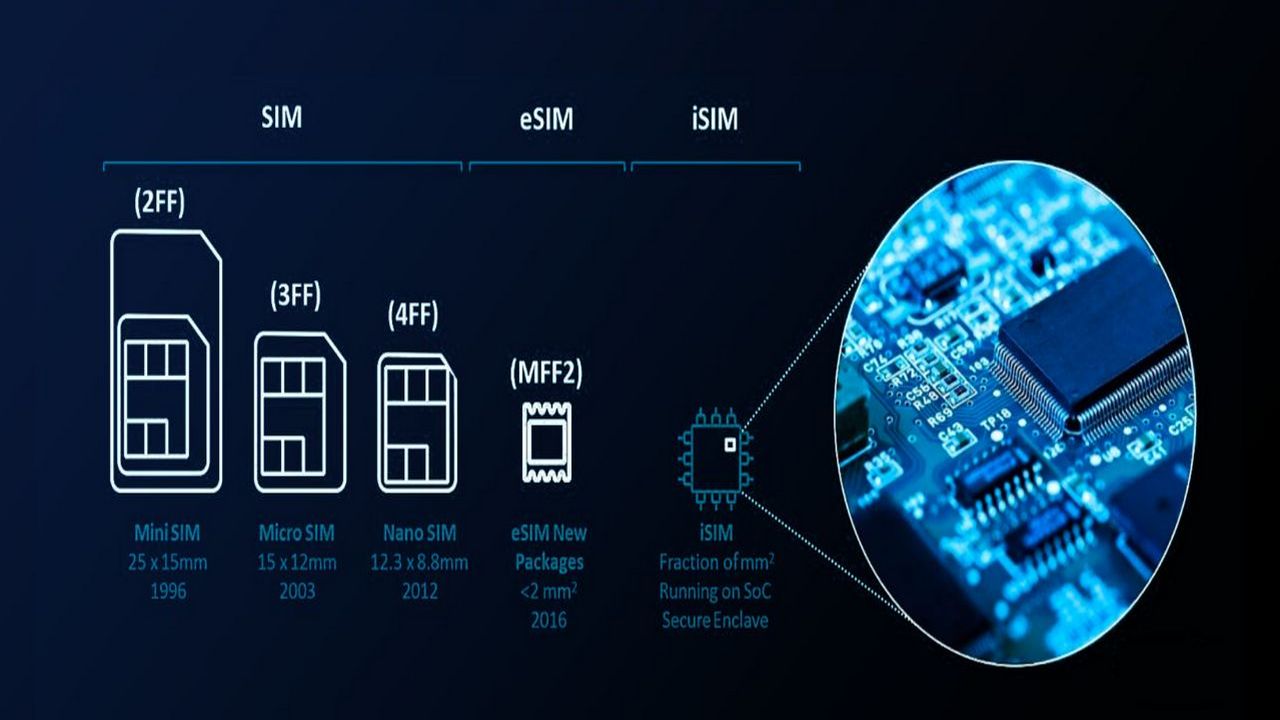
To comprehend the security nuances of eSIMs, it’s imperative to first understand the technology behind them. In contrast to conventional SIM cards, eSIMs are integrated directly into devices, eliminating the necessity for physical cards. This compact, built-in solution enables seamless switching between mobile carriers, enhancing user convenience. The security foundation of eSIMs lies in their tamper-resistant hardware, making them challenging targets for physical attacks.
Myth 1: Hacking eSIMs Is a Walk in the Park
Contrary to popular belief, hacking eSIMs is no easy feat. The tamper-resistant hardware, coupled with robust encryption protocols, acts as a formidable barrier against unauthorized access. While no system is entirely invulnerable, the security measures in place make hacking eSIMs a complex and resource-intensive endeavor. As technology evolves, so too do the defenses against potential threats, ensuring that eSIMs remain a secure means of connectivity.
Myth 2: Tracking Through eSIMs Is a Silent Invasion of Privacy
Privacy concerns often shroud discussions about embedded SIM cards. However, it’s essential to dispel the myth that eSIMs facilitate covert tracking. Unlike GPS trackers, eSIMs do not inherently provide real-time location data. The primary function of eSIMs is to manage and authenticate connectivity between devices and carriers. Tracking a user’s location through eSIMs would require accessing additional layers of information beyond their intended purpose.
The Role of Encryption in eSIM Security

Encryption stands as a sentinel guarding eSIMs against potential breaches. The data exchanged between eSIMs and carriers is encrypted, rendering it unreadable to unauthorized entities. The encryption protocols employed in eSIM technology undergo rigorous testing to ensure their efficacy. As a result, intercepting and deciphering communication between eSIMs and carriers demands a level of sophistication that is beyond the reach of the average hacker.
Securing eSIMs Against Remote Attacks
While physical security is crucial, the digital realm poses its own set of challenges. Remote attacks on eSIMs, often associated with malware or phishing attempts, necessitate additional layers of protection. Regular software updates, multifactor authentication, and user education play pivotal roles in fortifying eSIMs against remote threats. By staying vigilant and implementing best practices, users can further bolster the digital shield protecting their embedded SIM cards.
In the ever-connected landscape of today, the security of our digital interactions remains paramount. Debunking myths surrounding eSIMs is crucial in fostering a deeper understanding of their robust security measures. As technology advances, so does the sophistication of security protocols, ensuring that eSIMs continue to be a reliable and secure cornerstone of modern connectivity. Understanding the intricacies of eSIM technology empowers users to embrace the future of connectivity with confidence, knowing that their digital interactions are safeguarded against hacking and tracking threats.