Welcome to our comprehensive guide on building a secure web application. In today’s digital landscape, application security is of utmost importance. With the increasing reliance on web programming and website development, it is crucial to understand the best practices for ensuring that your web applications are protected from potential threats. In this article, we will provide you with valuable insights and tips to help you build a secure web application that can withstand the ever-evolving cyber threats.
Understanding Application Security
Before diving into the nitty-gritty of building a secure web application, it is essential to understand what application security entails. Application security refers to the measures and practices taken to protect web applications from unauthorized access, data breaches, and other potential security threats. It involves identifying vulnerabilities, implementing robust security controls, and regularly monitoring and updating your application’s security measures.
Web programming plays a significant role in creating a secure web application. It is essential to have a thorough understanding of the underlying technologies, such as HTML, CSS, JavaScript, and backend frameworks, to ensure a robust and secure application architecture. By adhering to best practices in web programming, you can build a solid foundation for your secure web application.
Common Security Threats for Web Applications
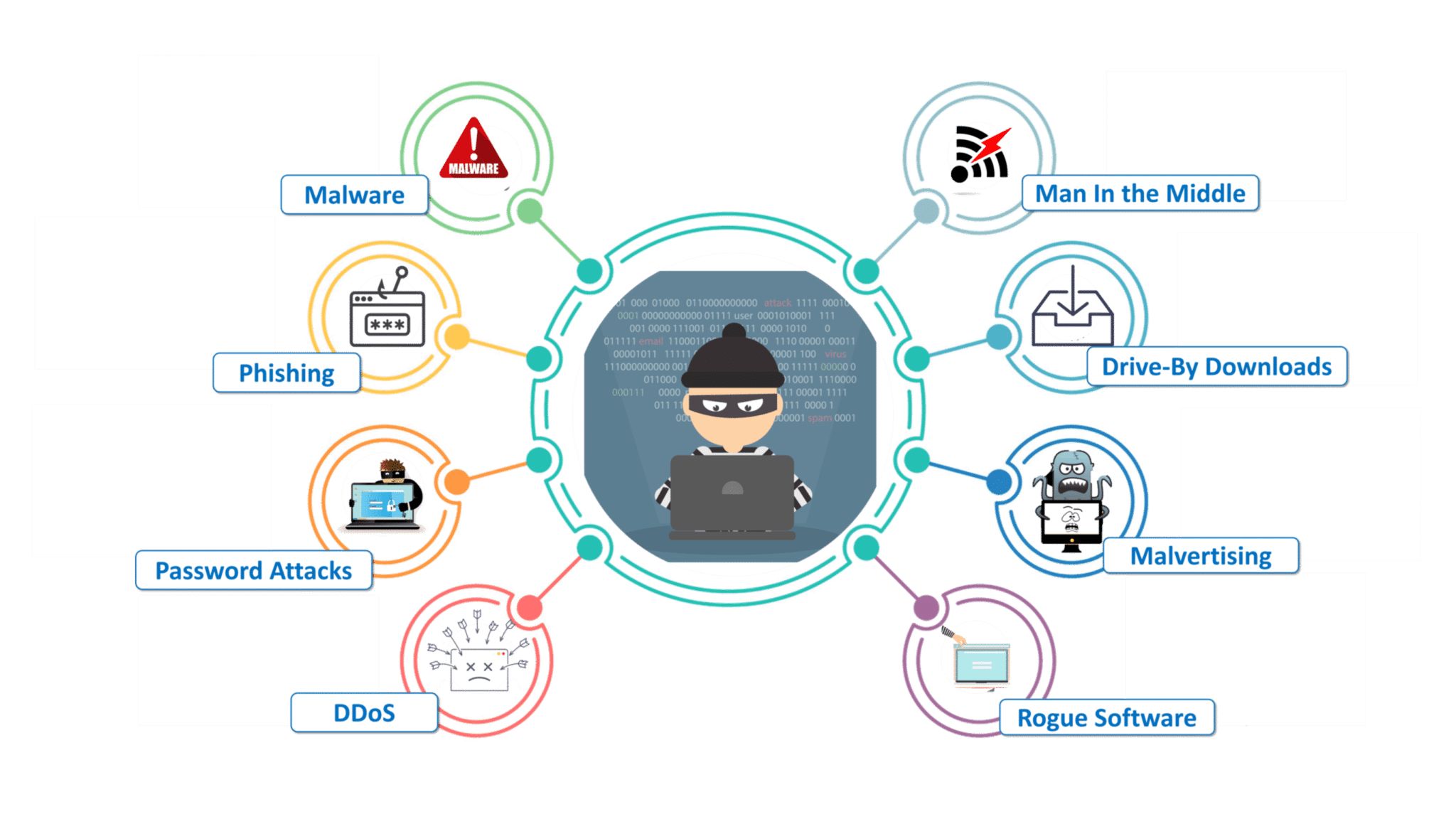
Web applications face a wide range of security threats that can have severe consequences if not adequately addressed. Some of the common threats include:
- Data breaches: Hackers exploit vulnerabilities in web applications to gain unauthorized access to sensitive user information.
- SQL injections: Attackers use malicious SQL queries to manipulate a web application’s database and retrieve or modify sensitive data.
- Cross-site scripting (XSS): This type of attack involves injecting malicious scripts into a web application to steal user data, spread malware, or perform other malicious activities.
- Session hijacking: By intercepting session cookies or session IDs, attackers can gain unauthorized access to user accounts.
- Brute force attacks: Hackers attempt to gain access to a web application by systematically trying different combinations of usernames and passwords.
Understanding these security threats is crucial for developing effective countermeasures. By addressing vulnerabilities and implementing robust security measures, you can protect your web application and its users from these potential risks.
Best Practices for Building Secure Applications
Now that we have explored the common security threats, it’s time to dive into the best practices for building secure web applications. Here are our top tips:
1. Implement Robust Authentication and Authorization Mechanisms
One of the key pillars of application security is ensuring robust authentication and authorization mechanisms. Implementing strong passwords, multi-factor authentication, and secure session management are vital for protecting user accounts from unauthorized access. Additionally, two-factor authentication, such as using biometrics or SMS verification codes, adds an extra layer of security to user authentication processes. By implementing these measures, you significantly reduce the risk of unauthorized access to your web application.
2. Secure Data Storage and Encryption
Securing sensitive user data is of paramount importance in web application development. Utilize industry-standard encryption algorithms to protect data both at rest and in transit. Implementing encryption measures ensure that even if an unauthorized entity gains access to your database, the data remains unreadable without the encryption keys. Additionally, consider practices such as salting and hashing passwords to further enhance the security of stored user credentials.
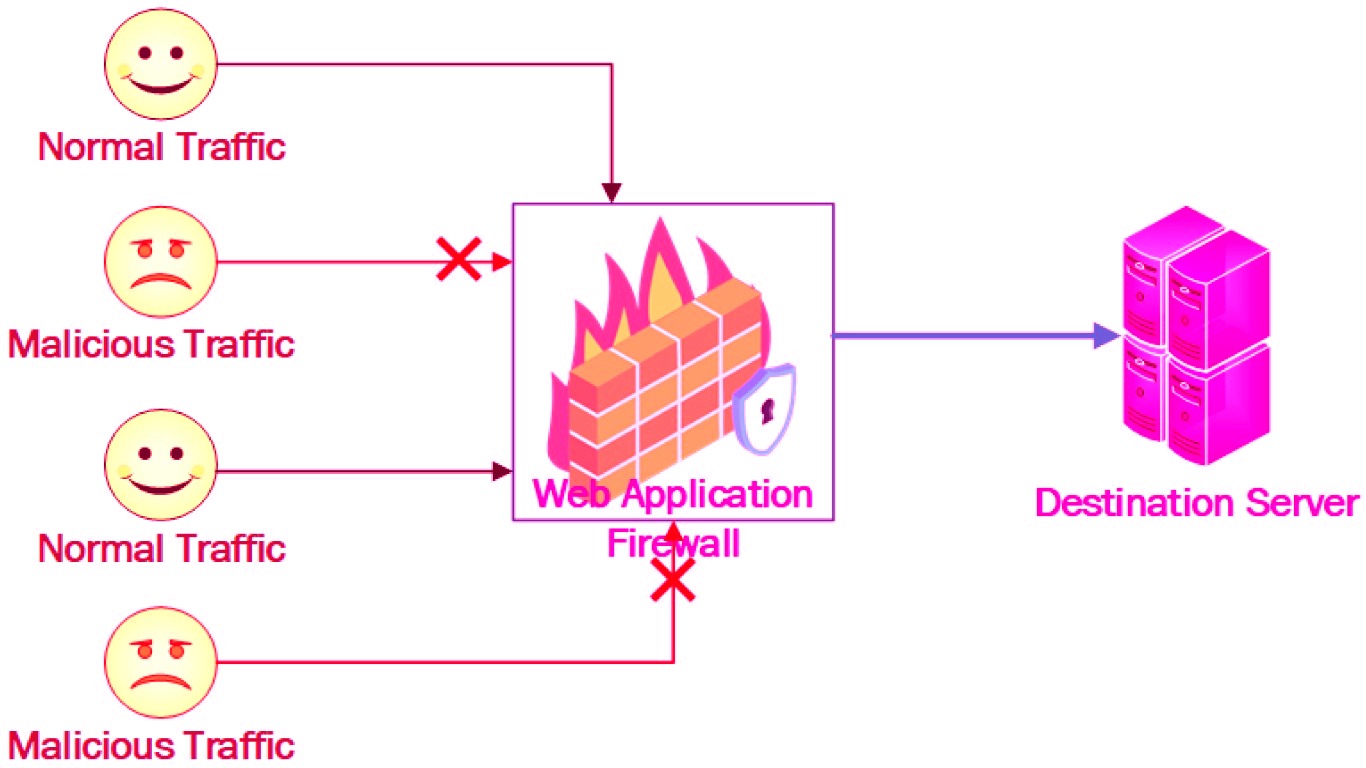
3. Implementing a Web Application Firewall
A web application firewall acts as the first line of defense against common security threats. By analyzing incoming requests and blocking potential attacks, a firewall safeguards your web application from malicious activities. It filters out potentially harmful traffic, such as SQL injections and cross-site scripting attempts, and can be customized to meet your application’s specific security needs. Implementing a web application firewall is a proactive measure that significantly mitigates the risk of security breaches.
4. Ensuring Secure Communication with SSL Certificates
Secure communication is vital for protecting sensitive user data. Implementing SSL certificates enables secure, encrypted communication between the web server and the user’s browser. This establishes trust and prevents eavesdropping, data tampering, and other potential threats. SSL certificates also play a role in search engine rankings, as major search engines prioritize websites that provide secure connections. By adding an SSL certificate to your web application, you not only enhance security but also improve its visibility and credibility.
Testing and Continuous Monitoring
Building a secure web application is an ongoing process. Regular testing and continuous monitoring are essential for identifying vulnerabilities and mitigating security risks. Conduct vulnerability scanning and penetration testing to simulate potential attacks and discover weaknesses in your application’s security posture. Additionally, perform regular security audits to ensure that your web application remains up to date with the latest security patches and protocols. By adopting a proactive approach to cybersecurity, you can stay one step ahead of potential threats and protect your web application and its users.
Building a secure web application requires a combination of technical expertise, best practices, and a proactive mindset towards application security. By understanding the common security threats, implementing robust security measures, and continuously monitoring your web application’s security, you can create an environment that protects user data and maintains the trust of your users. Investing time and effort into building a secure web application is essential in our increasingly digital world, where cybersecurity risks continue to evolve.